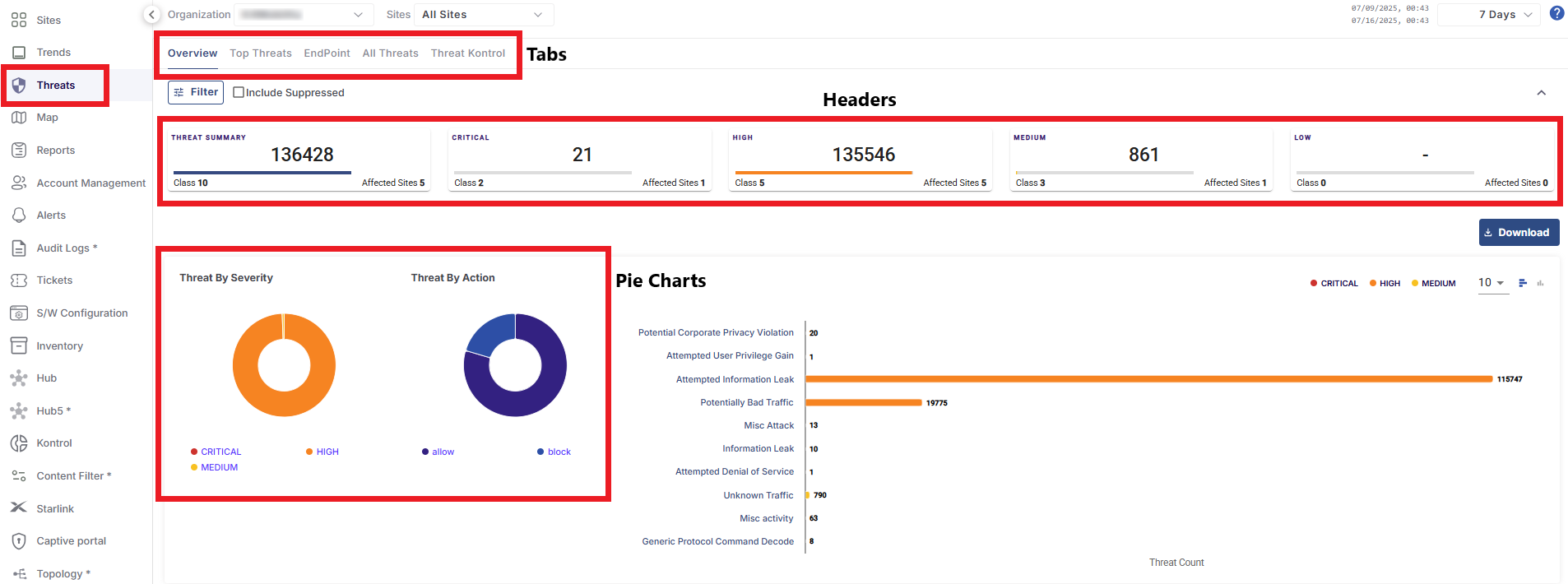
Threats
The Threats screen provides a consolidated view of all the threats received by the User’s system - shows the severity of the threats, the different classes of threats, Top threats and the log of all the threats received. Viewing such information about threats is essential for maintaining the security, performance, and reliability of the organization's network infrastructure.
Benefits of Threats Screen:
Detecting Intrusions: By monitoring network threats, users can detect intrusions, malware, or unauthorized access attempts. This enables proactive responses to threats before they can cause harm.
Quick Recovery: If a threat is detected, users can mitigate it quickly, ensuring the network stays operational or minimizing recovery time.
Audit Readiness: Regularly assessing network threats helps ensure that an organization can pass security audits and remain compliant with industry standards.
Resource Management: Some threats, like malware or rogue applications, can consume excessive bandwidth or CPU resources, reducing the performance of critical applications. By monitoring threats, network managers can identify and neutralize such issues, ensuring optimal network performance.
Preventing Network Slowdowns: Attackers might use techniques like traffic flooding to slow down networks. By identifying threats early, administrators can address issues that degrade network performance.
Risk Assessment: Monitoring threats helps identify vulnerabilities in the network's infrastructure, software, and configurations. This allows network administrators to patch or fix these weaknesses before attackers can exploit them.
Continuous Improvement: Threat visibility allows administrators to refine security protocols, improve network designs, and adopt better tools or practices over time.
Select the Threats option from the side bar. The Threats screen contains three tabs namely,
Overview
Top Threats
End Point
All Threats
Threat Kontrol
Threats
The filters are common for all three tabs.
In the Organization field, select the Organization or sub-organization from the dropdown menu. The logged in admin Organization is populated by default here. This is the organization corresponding to the email ID used to login.
The dropdown list consists of all the sub-organizations under logged in admin organization.
In the Sites field, select the required sites from the dropdown menu. The dropdown menu consists of all the sites associated with the selected Organization and sub-organizations.
Select the Period from the dropdown menu.
Please refer the below pages for more information about the tabs.
