K4 Edge Release 6.5.4
Release Notes of 6.5.4
Though 6.5.4 is the incremental release of 6.5.3, it is selectively released for EdgeFit product line as a beta release, which has some common features sets applicable across all the product lines. Refer to the 6.5.3 release notes for further details.
K4 Edge Release 6.5.3 - 6.5.3 Release Notes
Release Notes of 6.5.4 Build 109 (May 2024)
There were few bug fix releases made on 6.5.4 release. The following pointers primarily covers the enhancements/bug fixes done between build 56-79, between build 79-98 and build 98-109 as they were the primary releases widely used.
Enhancements between Build 56 - 79
CAN - Password change / management is supported for all user types. Prior to this, only Self created captive users were able to reset their password without admin approval
CAN - White label / Branding of User portal
Traffic Policy to support IP/Port configuration of subnet with wildcard 0.0.0.0/0:<port>. This configuration will be useful specifically to block all VPN traffic - ex. to block all WireGuard VPN traffic from the LAN network configure a policy of 0.0.0.0/0:51820 with deny option
Enhancements between Build 79 - 98
Gen2 K4 PEP enhancements based on feedback from Field Trial systems
Unknown App in Activity reports is further updated to reflect the protocols - Certain protocols such as VPN/STUN/HTTPS are reported as unknown. This is further categorized as Unknown-IPSEC, Unknown-STUN so that further analysis can be simplified
Events are sent to cloud for any System triggered system reboots and on System up as well
Cosmetic change - Aggregate Traffic policy is renamed to “Network Traffic Policy” wherever applicable
Enhancements between Build 98 - 109
WAN balancing/bonding updates moved from 10sec to 300sec (for systems having Starlink) - Less aggressive reweight to reduce system coredumps
System Health metrics on Cloud
Konnect Hub latest binary included - Address issues with WiFi Calling
Bug Fixes between 56 - 79
Correction for Content Filtering report on Cloud
Probe module crash in few scenarios causing the WAN connectivity loss
Hardening of Software Upgrade Process
Tower Scan failure on 5G Modem resulting in failure of Cellular service
Correction for DPI analytics / Activity Report
HA configuration on WAN sub interface causing duplicate MAC address causing WAN instability
Bug Fixes between 79 - 98
CAN user logout/dropping from network based of wrong/improper handling for inactivity detection logic
Edge Portal updated to remove the red banners on poor/broken connection and few alignments with poor links
Disk Usage/Log optimization and alerts on high resource usage (disk, CPU, memory, temperature)
Correction for Wireguard configuration to support network configuration
Correction for License expiry message showing incorrectly on Edge Portal
Bug Fixes between 98 - 109
Route Access network(s) configuration with different subnet lengths caused traffic issue - got corrected
On CAN User logout, the existing flows/sessions were getting cleared
Added error message in Config Restore section (General Settings) when backup of higher build is restored on previous build version
Starlink Mgmt IP configuration – can be dynamically updated
Update CAN Forgot Password popup (to address users not clicking Admin Approval by mistake)
Port Forwarding settings includes the TCP/UDP protocol field as well
Correction for mismatch btw WAN Usage and DPI Usage
Correction for removing VPN mapping on removal of Access N/W
No NAT WAN Interfaces
With 6.5.4 release, the WAN interface can be configured to bypass the NAT so that the Access Network traffic with their original IPs will be visible upstream on the WAN side. Note: With this configuration enabled, make sure the routes are configured on the upstream (upstream router on the WAN side) to route the traffic back appropriately. By default this configuration is disabled on all WAN interfaces.
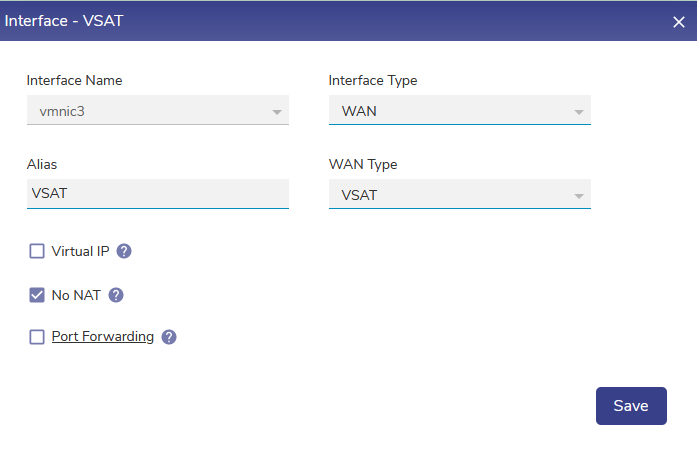
No NAT Configuration
Inbound Port Forwarding on WAN Interfaces
On the WAN interface, port forwarding can be enabled to forward the incoming port matching with the configured entry to be forwarded to a system on the Access Network side.
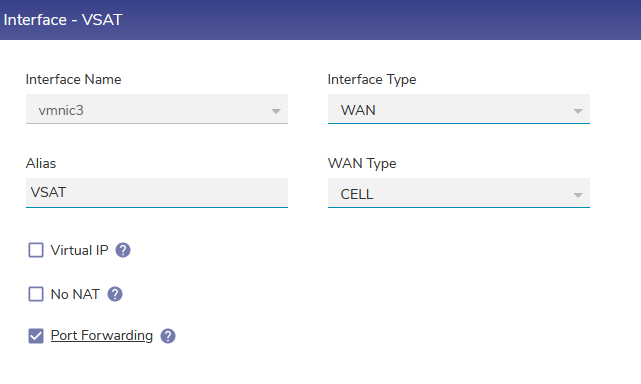
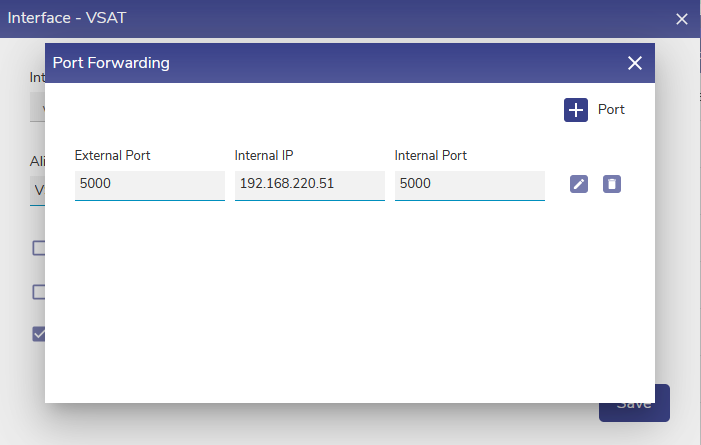
Port Forwarding Configuration
Firewall Settings
Firewall configuration is moved out from the General Settings and is shown as a separate configuration with the following enhancements for ease of use.
Firewall rules can be uploaded/downloaded in the CSV format
While adding the rules manually, multiple entries can be created from the same pop-up
Firewall rule can be cloned / duplicated
Firewall rule can be modified to create bidirectional rule - with source and destination swapped
Firewall rule can be disabled (if not used)
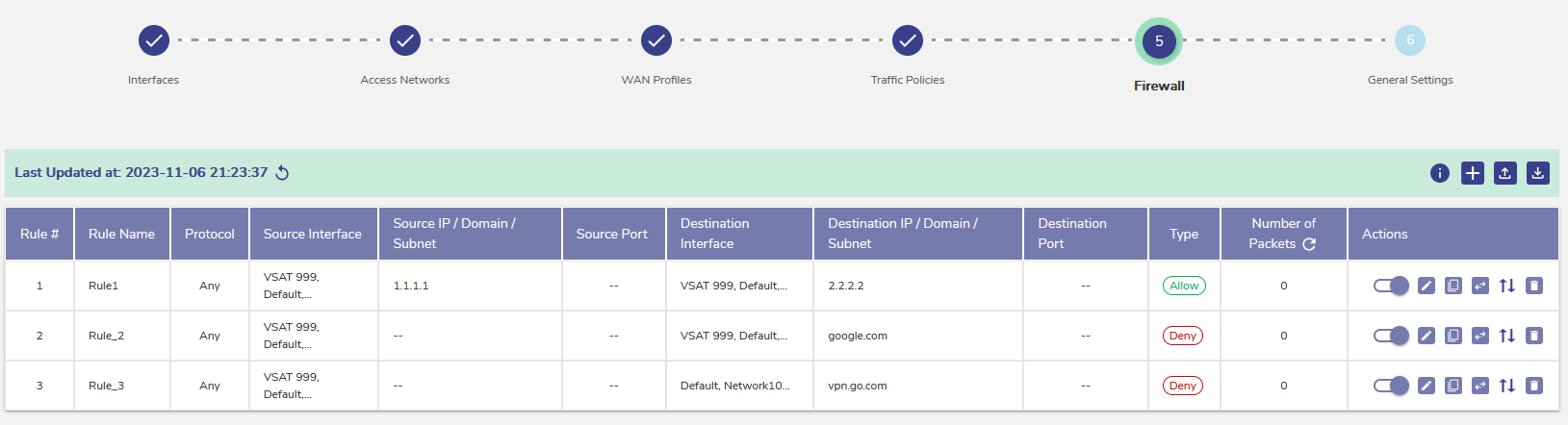
Firewall Configuration
IPSec Client Support
Apart from Wireguard Server/Client support, IPSec Client is supported with 6.5.4 release. VPN configuration is under Configuration Wizard → General Settings → VPN. Click on “New Connection” to configure the IPSec parameters for the tunnel. Refer to the <TBD> for details of all the fields.
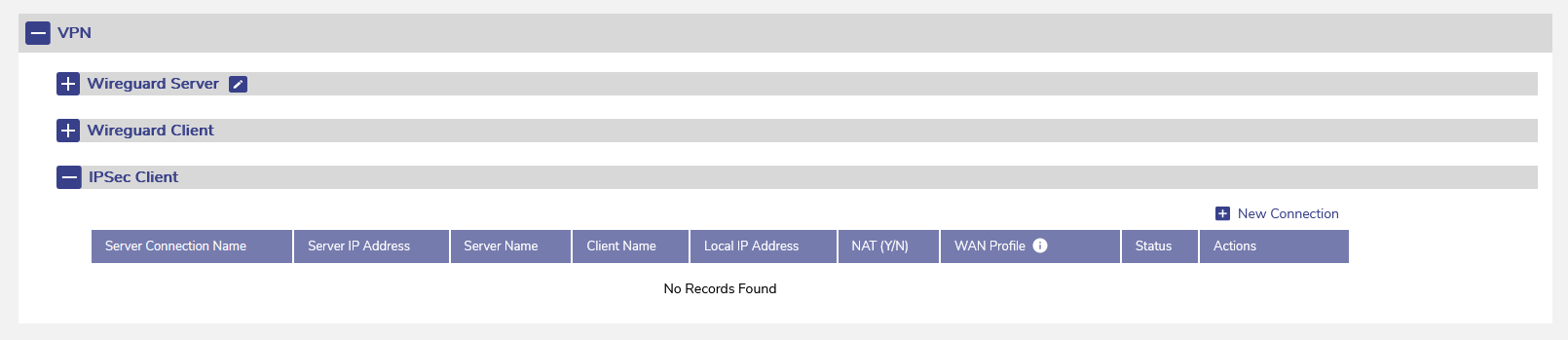
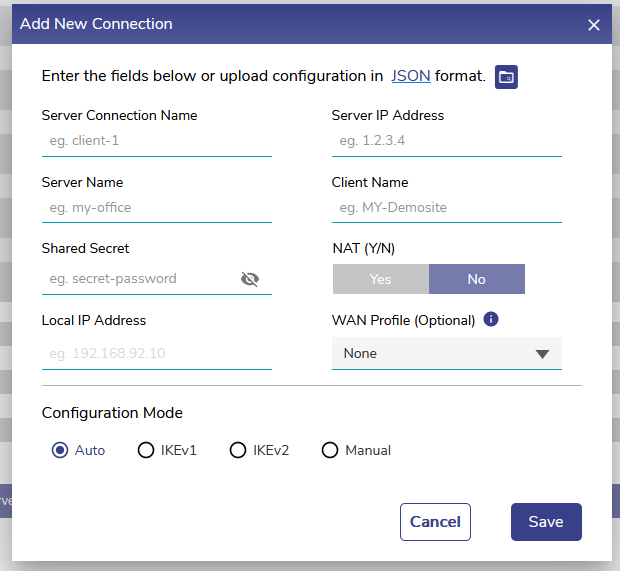
IPSec Client Support
Security Enhancements
Usage Status provides IP:Protocol information along with the Port details
User Traffic Threat analysis and risk score is shared to the cloud / Will be visible in sport under the Activity report
SNMP is disabled by default. In the prior release, if the customer has configured non default community string (public), then the configuration is retained.
Enhancements on Captive Access Network
With the 6.5.4 release, admin can create Captive user accounts without setting the passwords and enable the user to configure the password on their first login. From the end user front, they need to pick the option of “First Time Login” to configure the password and go thru the same flow as of now. This reduces the burden on the Captive administrator in new user account configuration.
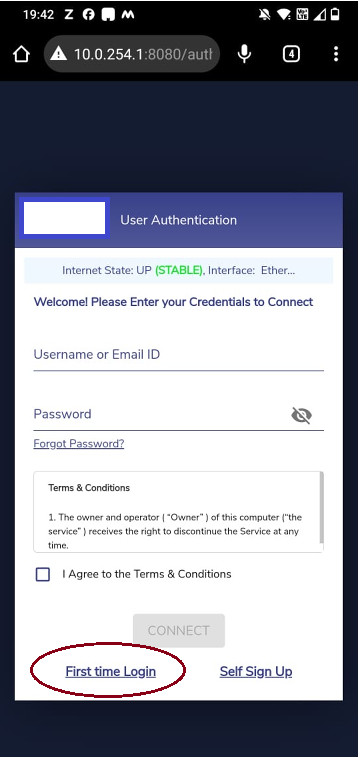
First Time Login
Bug Fixes/Enhancements
Along with the above features, following bug fixes / enhancements are included in this release:
All usage reporting is moved to base 10 to be inline with Starlink cloud/app/service portal
Internet Dashboard report/pie charts provides the WAN usage along with the Access network usage as well
Link can be reset for the USB based Ethernet interfaces
Few failure scenarios related to Software update handled
New revision of K4 PEP is installed but disabled by default. Intent is to trial this on few sites and make it as default in subsequent release. Along with this change, performance charts show the probe status of PEP
Edge Notification on software upgrades pushed to the cloud
Following issues are corrected
DNS black-hole on reboot/upgrade
SNMP failure of response not being sent over the same interface
SNMP String not getting displayed based on the user login
