Guide: Risk Score Overview
Keywords: EdgeOS, Kognitive Cloud
Kognitive Deep Packet Inspection solution utilizes nDPI with Netify optimization; with nDPI providing an application risk type and score for each flow analyzed. There are 50+ risk types identified with more coming, and each risk type has a set risk ‘level’ score, with the risk score being a numerical value that represents how ‘risky’ is a flow: the higher the score, the more “risky” the flow. Using this technique, one can spot flows that are more suspicious and may require device/network attention.
Kognitive DPI system calculates the top 5% flow risk average for each device in the network, and reports this in the Service Portal Activity Report. From here, one can click each devices risk score value and the “risk type” are presented that are within that top 5% risks. If one requires more detail, a report can be generated including the flow data and thus all flow risks can be analyzed.
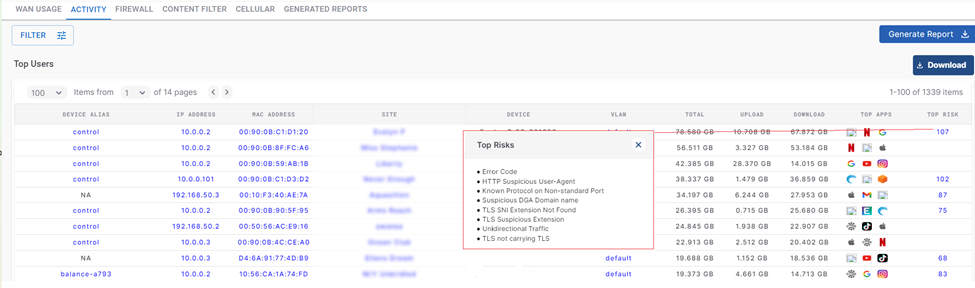
Activity
Flow Risk Scores and Types
The flow risk score and types are set by the nDPI development organization and is a relatively new concept that is evolving.
The current ‘Risk Type” values are listed here.
Netify ID | Risk | Severity | Score |
1 | XSS Attack | Severe | 250 |
2 | SQL Injection | Severe | 250 |
3 | RCE Injection | Severe | 250 |
4 | Binary App Transfer | Severe | 250 |
5 | Known Proto on Non Std Port | Medium | 50 |
6 | Self-signed Cert | High | 100 |
7 | Obsolete TLS (v1.1 or older) | High | 100 |
8 | Weak TLS Cipher | High | 100 |
9 | TLS Cert Expired | High | 100 |
10 | TLS Cert Mismatch | High | 100 |
11 | HTTP Suspicious User-Agent | High | 100 |
12 | HTTP Numeric IP Address | Low | 10 |
13 | HTTP Suspicious URL | High | 100 |
14 | HTTP Suspicious Header | High | 100 |
15 | TLS (probably) Not Carrying HTTPS | Low | 10 |
16 | Suspicious DGA Domain name | High | 100 |
17 | Malformed Packet | Low | 10 |
18 | SSH Obsolete Cli Vers/Cipher | High | 100 |
19 | SSH Obsolete Ser Vers/Cipher | Medium | 50 |
20 | SMB Insecure Vers | High | 100 |
21 | TLS Suspicious ESNI Usage | Medium | 50 |
22 | Unsafe Protocol | Low | 10 |
23 | Suspicious DNS Traffic | High | 100 |
24 | Missing SNI TLS Extn | Medium | 50 |
25 | HTTP Suspicious Content | High | 100 |
26 | Risky ASN | Medium | 50 |
27 | Risky Domain Name | Medium | 50 |
28 | Malicious JA3 Fingerp. | Medium | 50 |
29 | Malicious SSL Cert/SHA1 Fingerp | Medium | 50 |
30 | Desktop/File Sharing | Low | 10 |
31 | Uncommon TLS ALPN | Medium | 50 |
32 | TLS Cert Validity Too Long | Medium | 50 |
33 | TLS Suspicious Extn | High | 100 |
34 | TLS Fatal Alert | Low | 10 |
35 | Suspicious Entropy | Medium | 50 |
36 | Clear-Text Credentials | High | 100 |
37 | Large DNS Packet (512+ bytes) | Medium | 50 |
38 | Fragmented DNS Message | Medium | 50 |
39 | Text With Non-Printable Chars | High | 100 |
40 | Possible Exploit | Severe | 250 |
41 | TLS Cert About To Expire | Medium | 50 |
42 | IDN Domain Name | Low | 10 |
43 | Error Code | Low | 10 |
44 | Crawler/Bot | Low | 10 |
45 | Anonymous Subscriber | Medium | 50 |
46 | Unidirectional Traffic | Low | 10 |
Flow Risk Score – Risk Threat Range
The nDPI defines the integrated threat or risk score in a range of 0 to 250.
NDPI Score Risk | Score |
LOW | 10 |
MEDIUM | 50 |
HIGH | 100 |
SEVERE | 150 |
CRITICAL | 200 |
EMERGENCY | 250 |
