Guide: IPS Deployment
Overview
This guide explains how to deploy and configure the Intrusion Prevention System (IPS) on an KonnectOS device to protect your network from threats by monitoring traffic and blocking malicious activity. It covers enabling IPS in the KonnectOS Portal, selecting appropriate detection and prevention policies, and managing advanced options such as blocklists, allowlists, and remote logging. By following this guide, you will be able to set up an effective IPS that detects suspicious behavior, prevents network intrusions, and provides logging for security analysis and reporting.
The Intrusion Prevention System (IPS) helps protect your network by monitoring traffic in real time and blocking threats such as malware or unauthorized access attempts. You can enable and configure IPS directly from the KonnectOS Portal.
This guide walks you through the steps to set up IPS, choose the right policy, and manage advanced settings like blocklists, allowlists, and remote logging.
Key Functions of IPS:
Detection: Monitors incoming and outgoing traffic for suspicious patterns or signatures that match known attack types (like malware, vulnerabilities, or exploits). These Signatures are updated frequently to ensure that the IPS defends against the latest threats.
Prevention: Once a threat is detected, the IPS can take action such as:
Blocking harmful traffic
Resetting connections
Sending alerts to administrators
Logging and Reporting: It logs details about the intrusion attempts for future analysis and creates reports for network administrators to review.
Configuration
Open your browser and log in to the KonnectOS Portal with your credentials.
From the side menu bar, click Security.
Select the IPS tab.
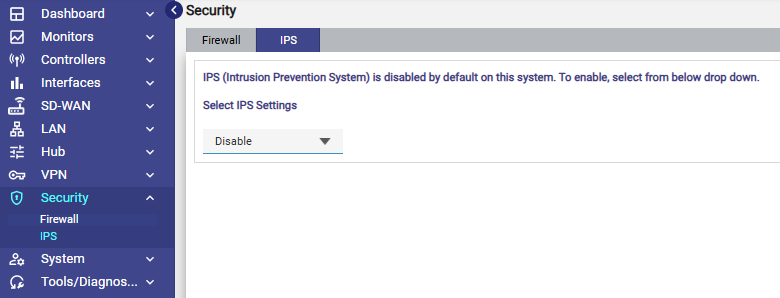
IPS
By default, IPS is turned off.
From the Select IPS Settings dropdown, choose Enable.
Once enabled, the IPS Configuration section becomes available.
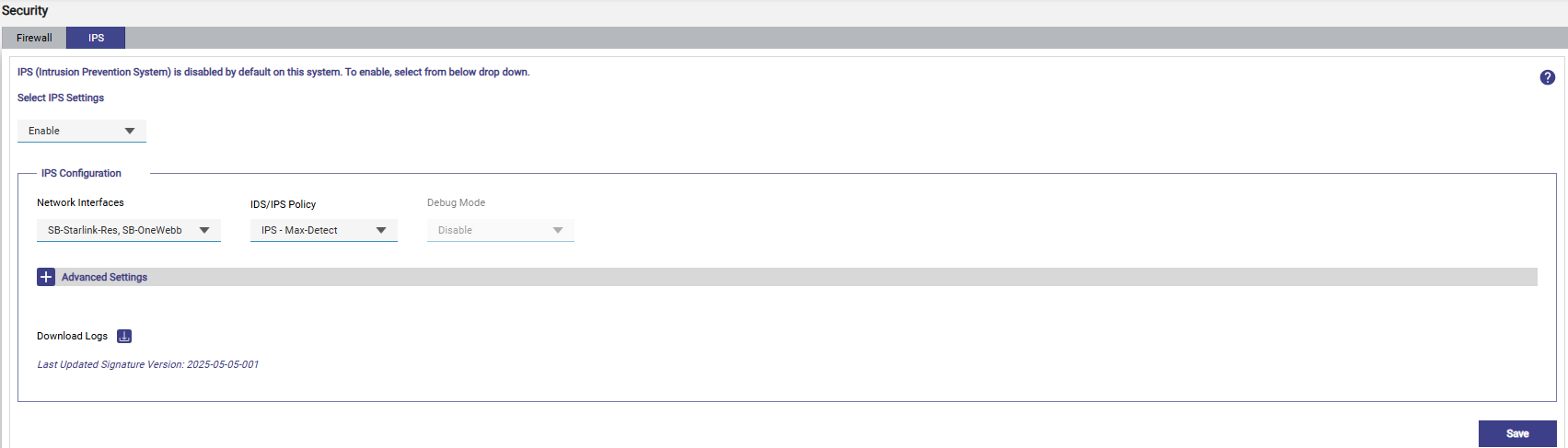
IPS Configuration Section
In the Network Interfaces dropdown, choose which interfaces you want IPS to monitor.
You’ll see both WAN interfaces and Access Networks configured in your system.
Please keep in mind: Enabling IPS on multiple interfaces will use more memory and CPU.
For best performance, limit IPS to two interfaces or fewer.
Refer to the benchmark details later in this guide for more insights.
From the IDS/IPS Policy dropdown, select how IPS should detect and block threats:
IDS – None
Use this option if you only want to detect threats (not block them). Helpful for troubleshooting false positives.IPS
Balanced (Recommended)
Default setting. Provides strong security with good performance. Best starting point.Connectivity
Prioritizes performance and reduces false positives. Choose this if you notice performance issues.Security
Provides maximum protection, suitable for networks where security is more important than performance. May cause false positives or noisy alerts.Max Detect
Tests for every possible threat but may cause many false positives. Best for testing environments, not production.
👉 Tip: Start with Balanced. If you notice network slowdowns, switch to Connectivity.
Debug Mode is only available if you select IDS – None.
Turn this on if you need detailed logs for troubleshooting.
Click Advanced Settings to open extra options.
-20250925-144932.png?inst-v=b22aba2e-4bdd-4e01-8fe1-6fa71c160677)
Advanced Settings
Blocklist
Set Blocklist to Enable if you want to block specific IP addresses.
Enter the IP addresses in the text box, or upload them in bulk using a CSV file.
Use this if you see unwanted IPs repeatedly probing your network.
Allowlist
Set Allowlist to Enable if you want to always allow traffic from specific IP addresses.
Enter the IP addresses in the text box, or upload them using a CSV file.
Common example: Allow a trusted file server that IPS might accidentally block.
Note: Allowlist always takes priority over Blocklist.
Toggle Remote Logging on if you want IPS alerts sent to a remote syslog/rsyslog server.
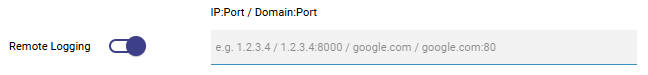
Remote Logging
Enter the server address in IP:Port or Domain:Port format.
Make sure the remote syslog server is configured to accept inbound logs.
Logs are sent with local0 as the facility.
An example for the remote rsyslog configuration is given below:
$template RemoteLogs,"/var/log/%HOSTNAME%/%PROGRAMNAME%.log"
*.* ?RemoteLogs
& ~
# provides UDP syslog reception
module(load="imudp")
input(type="imudp" port="514")
# provides TCP syslog reception
module(load="imtcp")
input(type="imtcp" port="514")
Click the Download Logs icon to save IPS logs locally for review.
After making your changes, click Save at the bottom of the page.
License Requirement
IPS features are available only with:
Edge Secure Enterprise license, or
Hub Secure Enterprise license
Make sure your device is registered with one of these licenses to use IPS.
You’ve now enabled and configured IPS. Your network traffic will be actively monitored, and threats will be detected and blocked based on the policy you selected.
IPS Performance Benchmarks and Recommendations
IPS performance depends on two main factors:
The IPS policy you select (Balanced, Connectivity, Max Detect, or Security).
The number of interfaces you enable IPS on.
Below are benchmark results for an Edge Pro device with 100 devices and 100 Mbps throughput.
Benchmark Results
Balanced or Connectivity Policy (Recommended)
LAN only → ~2% CPU, 5% Memory
LAN + 1 WAN → ~10% CPU, 10% Memory
LAN + 3 WANs → ~30% CPU, 25% Memory
💡 Best choice for most users. Provides good protection with low resource usage.
Max Detect or Security Policy
LAN only → ~30% CPU, 20% Memory
LAN + 1 WAN → ~30% CPU, 20% Memory
LAN + 3 WANs → ~30% CPU, 25% Memory
⚠️ These modes are much heavier on performance. Use only if you need maximum threat detection and are willing to handle more false positives.
Recommendations for Edge Pro Users
Start with Balanced
Offers strong security without high CPU load.
Fewer false positives compared to Max Detect or Security.
Focus on LAN interface
WAN interfaces are usually protected by carrier NAT, so the bigger risk comes from devices inside your LAN.
Running IPS on LAN alone gives you the biggest security gain with minimal performance cost.
Expect minimal impact
With Balanced policy + LAN-only monitoring, CPU and memory usage remain low while still improving security significantly.
When to Upgrade
If you need more interfaces monitored or want to use heavier security policies (Max Detect or Security), consider moving to:
Edge Pro2, or
Focus
Both have 2x the CPU and memory compared to Edge Pro, making them better suited for demanding IPS workloads.
